Scary new malware infects smartphones and hijacks router when connected to Wi-Fi
According to a report from Strategy Analytics for the third quarter of 2016, Google's Android mobile operating system now holds 87.5 percent of the global market share of smartphones. This means that globally, nine in 10 smartphones are running various versions of Android.
Impressive figures indeed due to the sheer volume of Android handsets circulating around the world. Unfortunately, due to this massive popularity, Android is also a common target for malware, viruses, trojans and all that fun stuff cybercriminals are known for.
Cyber scam tactics evolve, for sure, and this recently outed Android trojan proves just that - malware creators will never run out of ideas to indiscreetly steal money from you.
Meet the Switcher
The new Android trojan, discovered and nicknamed the Switcher trojan by SecureList researchers, is reported to secretly infect gadgets, but surprise, that's not its end goal. Its real purpose is to infect the Wi-Fi routers the compromised gadgets are connected to, then, in turn, redirect all the users of the network to poisoned sites.
According to the researchers, there are currently two versions of the malware circulating in the wild. In total, both versions have successfully compromised 1,280 Wi-Fi networks so far, mostly in China.
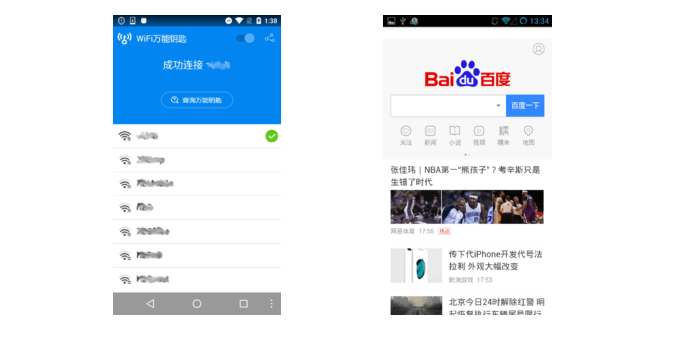
Photo credit: SecureList
One version pretends to be the mobile app for Chinese search engine Baidu (com.baidu.com) while another version masquerades as an app used for locating and sharing Wi-Fi login information (com.snda.wifilocating).
When a victim unwittingly downloads and installs either one of these apps it proceeds to search for and attack any Wi-Fi router the Android gadget is connected to.
How does Switcher operate?
First, the malware tries to guess the router's administration web interface password in an attack called brute-forcing - the inputting of thousands upon thousands of variations of character sequences in search of a password match.
(Switcher apparently uses Javascript code to brute-force passwords. The current code used only works on the web interfaces of TP-Link brand Wi-Fi routers but this may change over time.)
If the malware successfully cracks the admin password, it proceeds to change the primary address of the router's DNS server to those of the attackers and, for backup in case the primary goes down, the secondary DNS server is set to Google's (8.8.8.8).
(DNS or the Domain Name System is the way the internet converts readable names to numbers commonly referred to as a website's IP address. DNS servers basically work as the internet's phone books.)
After the malware is done with the router reconfiguration, all traffic from any device connected to the Wi-Fi network - computers, smartphones, tablets and other smart appliances regardless of model - is then rerouted to the attackers' DNS servers, which can then be used to serve up fake websites for phishing, adware scams and site redirection.
Basically, if your router's DNS servers have been switched to the attackers', they can hijack and redirect victims to any site they want.
What to look out for
This new Switcher trojan tactic is unique since it doesn't attack a gadget directly but instead, compromises a whole network.
This means even non-infected devices, as long as they're on the same compromised Wi-Fi network, could fall victim to the attackers' designs, leading to even more infections.
As usual, please refrain from downloading and installing Android apps from unknown third-party sources. Only download apps from official app stores like Google Play and check user feedback too before installing.
Aside from the two malicious apps to avoid, the security researchers also recommend users to check their router's settings for these DNS server addresses:
- 101.200.147.153
- 112.33.13.11
- 120.76.249.59
If you happen to spot any of these DNS addresses on your router's settings, they urge you to notify the Wi-Fi network owner or contact your internet provider for support.
Additionally, as we always advise here at komando.com, change your router's default administration username and password.
Likewise, check for and apply router firmware updates regularly, preferably at least once every three months.
More must-read articles:
Phishing scammers tried to target my studios - I saw the signs, will you?
Backdoor malware infecting this popular tablet brand
Sony's social media hack leads to embarrassing blunder


No comments:
Post a Comment